Archives for Joy Matthews-López, Ph.D.
May 5, 2017 | Published by Joy Matthews-López, Ph.D. |
|
|
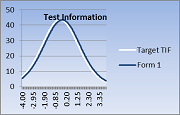
by Joy Matthews-López, PhD, and Vince Maurelli, MSc How forms are assembled and delivered are important components of an exam program’s... View Article
|
March 15, 2017 | Published by Joy Matthews-López, Ph.D. |
|
|
By Christine Depascale, MS, and Joy Matthews-López, PhD Low-volume examination programs face challenges that don’t necessarily apply to mid- to large-volume... View Article
|
September 23, 2016 | Published by Joy Matthews-López, Ph.D. |
|
|
Co-authored by Joy Matthews-López and David Cox One of the most common criticisms of the standard multiple-choice (MC) item format... View Article
|
April 14, 2016 | Published by Joy Matthews-López, Ph.D. |
|
|
While translation is necessary and usually the main focus in a test adaptation/localization project, a perfect translation may not be... View Article
|
April 14, 2016 | Published by Joy Matthews-López, Ph.D. |
|
|
The primary role of psychometrics in the adaptation/localization process is to provide evidence that target and source forms are equivalent... View Article
|
March 10, 2016 | Published by Joy Matthews-López, Ph.D. |
|
|
Simply put, validity refers to the degree to which evidence supports the inferences we make from test scores. Such inferences... View Article
|
January 20, 2016 | Published by Joy Matthews-López, Ph.D. |
|
|
A test security plan is a comprehensive collection of policies, procedures, and documents that outline and guide actions related to test security. From the development of an exam’s blueprint to the reporting of scores, test security touches nearly every aspect of test development and the testing process. Trust is a prerequisite to interpreting scores, and without evidence to support the integrity and veracity of scores, trust is compromised. Without trust, credibility is compromised.
|
December 9, 2015 | Published by Joy Matthews-López, Ph.D. |
|
|
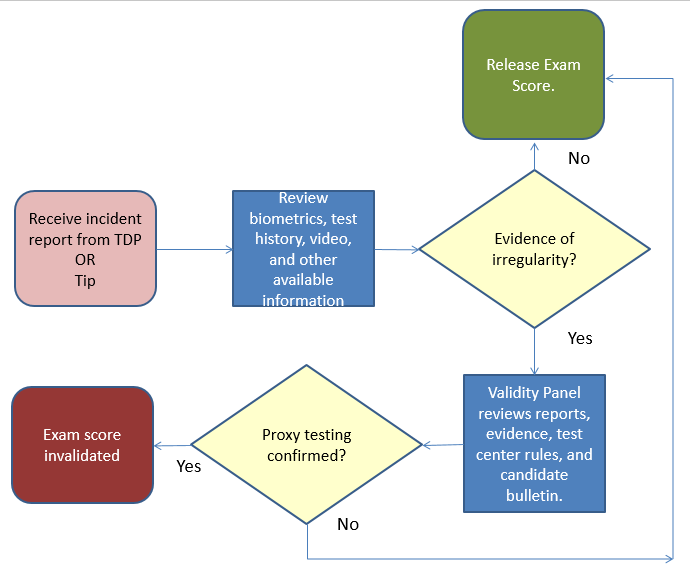
A test security flowchart is a visual protocol that is used to process anomalous (or aberrant) response vectors or incidents, and to do so in a consistent, controlled, unbiased way that contributes to the due diligence of assuring the integrity of resulting scores. By creating a flowchart for each recognized threat to a given program, anomalous or aberrant results can be processed consistently and fairly.
|
October 14, 2015 | Published by Joy Matthews-López, Ph.D. |
|
|
Joy Matthews-López, Ph.D. Please give a warm welcome to our newest contributor to From the Item Bank, Joy Matthews-López, Ph.D.,... View Article
|
|
|
|